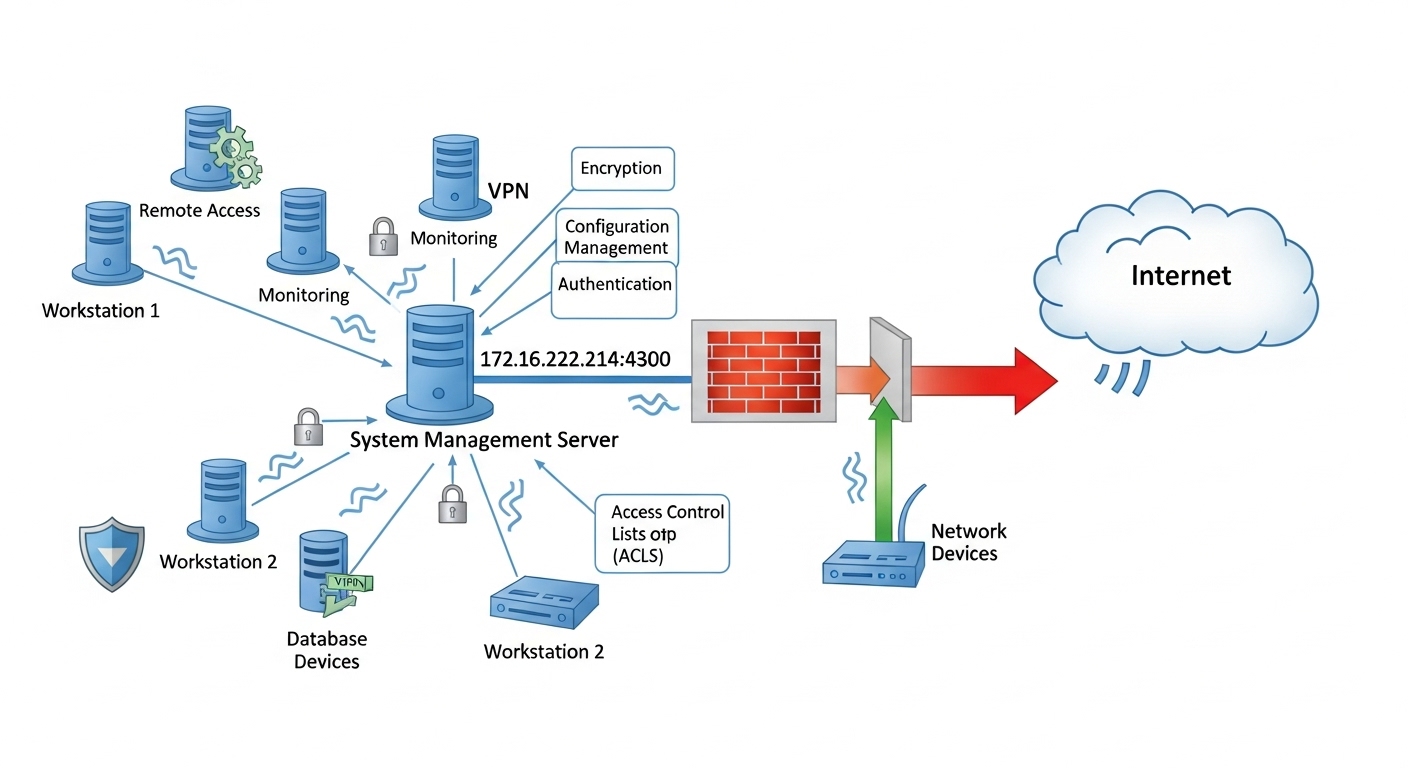
In the modern digital landscape, understanding IP addresses and ports like 172.16.252.214:4300 is crucial for anyone managing servers, networks, or web applications. This specific address format combines a private IP with a port number, helping devices and systems communicate effectively within local or restricted environments. By exploring how 172.16.252.214:4300 functions, its purpose, and the best practices for securing it, we can gain valuable insight into how local network configurations work behind the scenes.
What Does 172.16.252.214:4300 Represent?
The IP address 172.16.252.214 belongs to the private IP range defined by the Internet Assigned Numbers Authority (IANA). These addresses are not accessible from the public internet but are instead used within internal networks such as company LANs, data centers, or personal setups. The number :4300 following the IP represents a port — a virtual door through which applications send and receive information. Therefore, 172.16.252.214:4300 likely points to a specific service or application running on port 4300 within a private network.
How 172.16.252.214:4300 Works in Network Communication
When a computer connects to another device using 172.16.252.214:4300, it sends requests through the designated port. Each port number, like 4300, can host a different service such as web servers, databases, or internal APIs. Within an enterprise setup, 172.16.252.214:4300 might correspond to a testing environment or a secure internal dashboard used by administrators.
Private IP addresses like 172.16.252.214:4300 ensure that internal traffic remains isolated from external threats. Only authorized users within the same network can access such endpoints, which adds an extra layer of security compared to public IPs.
The Importance of Port 4300 in System Management
Every port plays a unique role in communication. While common ports like 80 or 443 are used for web traffic, custom ports such as 4300 are often configured for specialized tools or backend operations. Using 172.16.252.214:4300 allows developers and IT teams to create a secure channel for internal operations without interfering with standard internet ports.
In many organizations, ports like 172.16.252.214:4300 are used for monitoring tools, internal APIs, or software updates. This segregation minimizes the risk of cross-interference between public-facing and private systems, enhancing both efficiency and control.
Security Measures for 172.16.252.214:4300
While 172.16.252.214:4300 exists within a private range, it’s still essential to maintain strong security practices. Misconfigurations or improper access permissions can expose internal systems to risks. Implementing firewalls, intrusion detection systems, and network segmentation helps protect the endpoint 172.16.252.214:4300 from unauthorized access.
System administrators should also ensure that only trusted users can connect to 172.16.252.214:4300. Regular security audits, encryption, and password-protected access points are key to maintaining the integrity of internal communications.
Common Use Cases of 172.16.252.214:4300
In corporate environments, 172.16.252.214:4300 might be used for database synchronization, internal reporting dashboards, or system health monitoring tools. Developers could also employ 172.16.252.214:4300 for application testing before deploying updates to production servers.
Educational institutions or laboratories might use 172.16.252.214:4300 for research servers that store confidential data. Because it operates on a private network, sensitive information remains safe from the broader internet, ensuring compliance with data protection standards.
Troubleshooting Connectivity Issues with 172.16.252.214:4300
When 172.16.252.214:4300 becomes unreachable, the issue could stem from misconfigured firewalls, blocked ports, or incorrect routing tables. Network administrators can use tools like ping, traceroute, or netstat to diagnose problems. Checking whether the service running on port 4300 is active is also crucial. Restarting the associated application or verifying network permissions often resolves connection issues related to 172.16.252.214:4300.
Best Practices for Maintaining Network Health
Keeping 172.16.252.214:4300 stable requires continuous monitoring. Using centralized logging tools helps administrators track performance, detect unusual traffic, and prevent downtime. Regular software updates and patch management ensure that vulnerabilities associated with 172.16.252.214:4300 are minimized. Moreover, documenting all configurations allows teams to quickly recover from unexpected errors or security breaches.
Conclusion
The IP and port combination 172.16.252.214:4300 highlights the intricate relationship between private networking, security, and communication management. Though it may seem like a simple identifier, it plays an essential role in organizing and securing internal digital operations. Understanding how 172.16.252.214:4300 functions, maintaining strong security controls, and applying proactive management techniques can significantly improve network performance and reliability.